Many organizations invest heavily in robust Active Directory backup solutions, creating daily snapshots and storing them for years. Yet despite these diligent efforts, they might still face catastrophic failures when attempting to restore from older backups. The culprit? A little-understood setting called Tombstone Lifetime.
In this comprehensive guide, I’ll explain why your lengthy backup retention policies might be giving you a false sense of security and how to properly align your Active Directory backup strategy with AD’s internal mechanisms.
Table of Contents
The Hidden Danger in Your AD Backup Strategy
Picture this scenario: A critical corruption in your Active Directory environment is discovered, but the issue began months ago. You confidently retrieve a backup from 10 months ago, before the corruption occurred, only to find that restoring it creates replication storms, inconsistencies, and potentially an even worse situation than before.
This isn’t a hypothetical scenario—it happens regularly to organizations that fail to understand the relationship between backup retention and Active Directory’s tombstone lifetime setting.
Understanding Tombstone Lifetime in Active Directory
When an object is deleted in Active Directory, it isn’t immediately erased from the database. Instead, it’s converted to a “tombstone” object. These tombstones serve a critical purpose: they inform other domain controllers during replication that the object has been deleted and should be removed from their copies of the directory as well.
By default, Active Directory keeps these tombstone objects for a specific period depending on the Windows Server version. After this period, they’re permanently removed during a garbage collection process.
Default Tombstone Lifetime by Windows Server Version
The default tombstone lifetime has evolved across different Windows Server versions:
| Windows Server Version | Default Tombstone Lifetime (days) | Notes |
|---|---|---|
| Windows 2000 Server | 60 | Original AD implementation |
| Windows Server 2003 | 60 | Same as Windows 2000 |
| Windows Server 2003 SP1/SP2 | 180 | Increased to accommodate larger networks |
| Windows Server 2003 R2 | 60 | Base version |
| Windows Server 2003 R2 SP2 | 180 | Increased with SP2 |
| Windows Server 2008 | 180 | Maintained the 180-day setting |
| Windows Server 2008 R2 | 180 | Same as Windows 2008 |
| Windows Server 2012 | 180 | Same as Windows 2008 R2 |
| Windows Server 2012 R2 | 180 | Same as Windows 2012 |
| Windows Server 2016 | 180 | Same as Windows 2012 R2 |
| Windows Server 2019 | 180 | Same as Windows 2016 |
| Windows Server 2022 | 180 | Same as Windows 2019 |
| Windows Server 2025 | 180 | Same as Windows 2022 |
Note: If you’ve upgraded your forest from an older version of Windows Server, the tombstone lifetime might still be set to 60 days unless manually changed. Always check your current setting rather than assuming the default.
This tombstone lifetime is a crucial but often overlooked component of your backup and recovery strategy.
The Critical Relationship Between Backups and Tombstone Lifetime
Here’s the essential relationship every AD administrator must understand:
If you restore an Active Directory backup that’s older than your tombstone lifetime setting, you risk serious replication issues and directory inconsistencies.
Why? Because when you restore an older backup:
- The restored DC includes objects that were deleted more than the tombstone lifetime ago
- The tombstone records for these deletions have already been garbage-collected
- Without these tombstone records, the AD replication process can’t properly reconcile the differences between DCs
- The result is a poisoned directory with inconsistent data across your domain controllers
In simple terms: Your backup retention period should never exceed your tombstone lifetime setting.
Configuring Tombstone Lifetime for Long-Term Restores
If your organization requires the ability to restore from backups older than 180 days (the default tombstone lifetime), you must modify this setting. Here’s how to check and modify your current tombstone lifetime:
- Open ADSI Edit
- Connect to the Configuration partition
- Navigate to:
CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=yourdomain,DC=com - Look for the
tombstoneLifetime - Modify the value to match your longest required backup retention period (in days)
For example, if you need to retain yearly backups, set this value to at least 365 or preferably 400 (to provide some buffer).
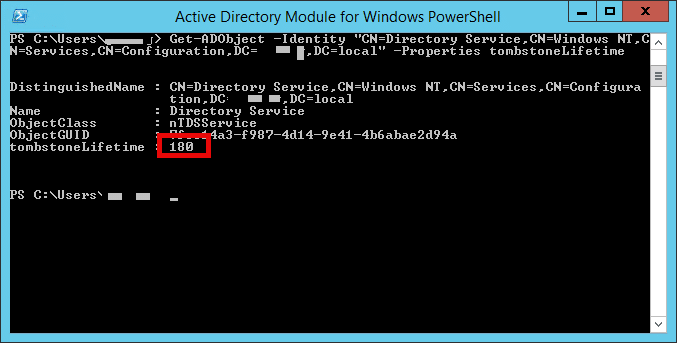
# PowerShell command to view current tombstone lifetime
Get-ADObject -Identity "CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=yourdomain,DC=com" -Properties tombstoneLifetime
# PowerShell command to set tombstone lifetime to 365 days
Set-ADObject -Identity "CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=yourdomain,DC=com" -Replace @{tombstoneLifetime=365}
Remember that increasing this value will increase the size of your Active Directory database, as deleted objects will remain in the directory for longer periods.
Best Practices for AD Backup Retention
When designing your AD backup retention policy, consider these best practices:
- Align with tombstone lifetime: Your longest backup retention should never exceed your tombstone lifetime setting
- Consider regulatory requirements: Some industries require data retention for specific periods
- Balance storage costs: Longer retention means higher storage costs
- Consider database performance impact: Longer tombstone lifetimes mean larger AD databases
- Adjust related settings: Also adjust the “deleted object lifetime” and “recycled object lifetime” settings for consistency
Implementing a Staggered Backup Strategy
A staggered (or tiered) backup retention strategy can provide an optimal balance between storage efficiency and recovery flexibility. Here’s a sample staggered approach:
| Backup Type | Retention Period | Number of Backups Kept |
|---|---|---|
| Daily | 30 days | 30 |
| Weekly | 3 months | 12 |
| Monthly | 1 year | 12 |
| Quarterly | 2 years | 8 |
This approach drastically reduces the number of backup points you need to store while still providing reasonable restore granularity. The key is ensuring your tombstone lifetime setting accommodates your longest retention period.
System State Backup Strategy
In addition to full VM backups, implementing a dedicated System State backup strategy is crucial for Active Directory environments. System State backups are typically smaller, faster to create and restore, and provide an efficient mechanism for recovering AD-specific components without restoring entire servers.
Recommended System State Backup Approach:
| System State Backup Frequency | Retention | Purpose |
|---|---|---|
| Twice daily (e.g., 12:00 and 16:00) | 7 days | For quick recovery from recent AD changes or corruption |
| Daily | 30 days | For recovering from issues discovered days after occurrence |
| Weekly | 90 days | For intermediate-term recovery needs |
| Monthly | Match tombstone lifetime | For long-term AD recovery scenarios |
Benefits of System State Backups for AD:
- Faster recovery: System State backups can often be restored more quickly than full VM restores
- Smaller storage footprint: They require significantly less storage space
- Targeted recovery: Allow you to recover just the AD components without affecting other server aspects
- Non-authoritative restore option: Support for both authoritative and non-authoritative restores
- Lower production impact: Generally create less performance impact during backup creation
When implementing System State backups, ensure you’re using a backup solution that properly supports Active Directory. For Windows Server environments, tools like Windows Server Backup with the System State option or specialized solutions like Azure Backup MARS agent provide reliable System State backup capabilities.
Remember that System State backups should complement, not replace, your full server backup strategy. The combination of both approaches provides the most comprehensive protection for your Active Directory environment.
Testing Your AD Recovery Strategy
No backup strategy is complete without regular testing. Schedule periodic recovery drills to ensure your backups are viable and your team is prepared for recovery scenarios.
Key tests should include:
- Full forest recovery: Test restoring your entire AD forest from backup
- Single DC recovery: Practice restoring just one domain controller
- Object-level recovery: Test recovering individual deleted objects
- Long-term backup recovery: Periodically test restoring from your oldest backups
Document the results of these tests and adjust your strategy as needed.
A robust Active Directory backup strategy requires more than just taking regular snapshots. Understanding the tombstone lifetime setting and its relationship to your backup retention policy is crucial for ensuring those backups remain usable when you need them most.
By aligning your backup retention with your tombstone lifetime setting, implementing a staggered backup approach, and regularly testing your recovery procedures, you can ensure your organization is truly protected against AD disasters.
Remember: Those year-old backups are only valuable if they can actually be restored without corrupting your entire directory!
FAQ
Can I set the tombstone lifetime to a very large value (like 10 years) just to be safe?
While technically possible, this would cause your Active Directory database to grow significantly larger, as deleted objects would be retained for an extended period. This can impact performance and increase storage requirements. It’s better to set a reasonable tombstone lifetime that aligns with your actual recovery needs.
What happens if I try to restore a backup that’s older than my tombstone lifetime?
The restore operation might complete, but you’ll likely experience replication issues, inconsistencies between domain controllers, and potentially lingering objects that cause ongoing problems. In the worst case, you might need to rebuild your entire Active Directory environment.
Do I need to adjust tombstone lifetime on all domain controllers?
No, this is a forest-wide setting stored in the configuration partition. When you modify it on one DC, it will replicate to all others.
Besides tombstone lifetime, what other settings should I be aware of for long-term AD recovery?
Also consider the “deleted object lifetime” (how long objects remain in the AD Recycle Bin) and “recycled object lifetime” (how long recycled objects are retained). These should typically be aligned with your tombstone lifetime setting.
When was the default tombstone lifetime changed from 60 to 180 days?
Microsoft increased the default tombstone lifetime from 60 to 180 days with Windows Server 2003 SP1, SP2, and Windows Server 2003 R2 SP2. This change was made to better accommodate larger and more complex Active Directory environments. However, if you upgraded from an original Windows Server 2003 or earlier without these service packs, your tombstone lifetime might still be set to 60 days unless manually changed.
How does Azure AD (Microsoft Entra ID) handle tombstone lifetime?
Azure AD operates differently and doesn’t use the same tombstone lifetime concept as on-premises Active Directory. However, when synchronizing with on-premises AD, the tombstone lifetime settings of your on-premises environment still matter for recovery scenarios.