Transport Layer Security (TLS) 1.2 is a secure protocol that encrypts data between clients and servers. Many modern security standards and compliance frameworks now require or strongly recommend using TLS 1.2 to protect sensitive information. In this post, we’ll walk through two PowerShell scripts:
Check-Tls12Configuration.ps1– A script to check if the correct registry settings for TLS 1.2 are in place.Enable-Tls12.ps1– A script that creates or updates registry values to enable TLS 1.2.
Table of Contents
Why TLS 1.2 Matters
- Security Compliance: Many compliance frameworks (e.g., PCI-DSS, HIPAA) require the use of strong encryption protocols.
- Better Performance: Newer versions of TLS can offer performance improvements over older protocols like SSL 3.0 or TLS 1.0.
- Compatibility: Microsoft services, .NET applications, and other modern software often require TLS 1.2 to function optimally.
Script 1: Checking TLS 1.2 Configuration
Below is a PowerShell script that reads specific registry keys to verify if TLS 1.2 is enabled and configured correctly. We’ve renamed the function to Get-Tls12RegistryValue
<#
.SYNOPSIS
Checks whether the required registry values for TLS 1.2 are present.
.DESCRIPTION
This script reads the .NET Framework and SCHANNEL registry entries to confirm
if TLS 1.2 is enabled and configured.
#>
Function Get-Tls12RegistryValue {
[CmdletBinding()]
Param
(
# Registry Path
[Parameter(Mandatory = $true, Position = 0)]
[string]
$RegPath,
# Registry Name
[Parameter(Mandatory = $true, Position = 1)]
[string]
$RegName
)
$regItem = Get-ItemProperty -Path $RegPath -Name $RegName -ErrorAction Ignore
$output = "" | Select-Object Path, Name, Value
$output.Path = $RegPath
$output.Name = $RegName
if ($regItem -eq $null) {
$output.Value = "Not Found"
}
else {
$output.Value = $regItem.$RegName
}
$output
}
# Collect registry settings for TLS 1.2
$regSettings = @()
# WOW6432Node .NET Framework Settings
$regKey = 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319'
$regSettings += Get-Tls12RegistryValue $regKey 'SystemDefaultTlsVersions'
$regSettings += Get-Tls12RegistryValue $regKey 'SchUseStrongCrypto'
# 64-bit .NET Framework Settings
$regKey = 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319'
$regSettings += Get-Tls12RegistryValue $regKey 'SystemDefaultTlsVersions'
$regSettings += Get-Tls12RegistryValue $regKey 'SchUseStrongCrypto'
# TLS 1.2 Server Settings
$regKey = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server'
$regSettings += Get-Tls12RegistryValue $regKey 'Enabled'
$regSettings += Get-Tls12RegistryValue $regKey 'DisabledByDefault'
# TLS 1.2 Client Settings
$regKey = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client'
$regSettings += Get-Tls12RegistryValue $regKey 'Enabled'
$regSettings += Get-Tls12RegistryValue $regKey 'DisabledByDefault'
# Output the results
$regSettings
How to Use
- Save the script as
Check-Tls12Configuration.ps1 - Open PowerShell with administrative privileges.
- Run the script:
.\Check-Tls12Configuration.ps1 - Review the output to see if TLS 1.2 registry settings are “Found” and set to the expected values (commonly
1for enabled,0for disabled-by-default settings).
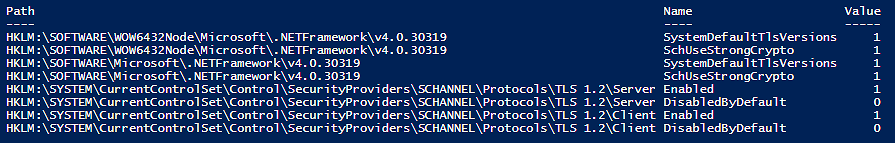
Example Output showing proper TLS1.2 configuration:
Script 2: Enabling TLS 1.2
If your check script indicates that TLS 1.2 isn’t properly configured, you can use the following script to enable it. This script creates or updates the necessary registry keys and values.
<#
.SYNOPSIS
Enables TLS 1.2 for .NET Framework and SCHANNEL.
.DESCRIPTION
This script will set the required registry values for TLS 1.2 to be used
by .NET applications and the Windows SCHANNEL security provider.
#>
# Ensure the .NET Framework registry paths exist and set the necessary properties
If (-Not (Test-Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319')) {
New-Item 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Name 'SystemDefaultTlsVersions' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Name 'SchUseStrongCrypto' -Value '1' -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319')) {
New-Item 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Name 'SystemDefaultTlsVersions' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Name 'SchUseStrongCrypto' -Value '1' -PropertyType 'DWord' -Force | Out-Null
# Ensure TLS 1.2 Server registry path exists and set the necessary properties
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server')) {
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Name 'Enabled' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Name 'DisabledByDefault' -Value '0' -PropertyType 'DWord' -Force | Out-Null
# Ensure TLS 1.2 Client registry path exists and set the necessary properties
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client')) {
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Name 'Enabled' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Name 'DisabledByDefault' -Value '0' -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.2 has been enabled. You must restart the Windows Server for the changes to take effect.' -ForegroundColor Cyan
How to Use
- Save the script as
Enable-Tls12.ps1 - Open PowerShell with administrative privileges.
- Run the script:
.\Enable-Tls12.ps1 - Restart the Windows Server. A system reboot is required for the changes to fully apply.
Summary
By combining these two scripts, you can quickly identify whether TLS 1.2 is correctly configured on your Windows Server and enable it if it is missing or disabled. Adopting TLS 1.2 is a best practice for modern security standards, ensuring encrypted connections and protecting sensitive information.
Key Takeaways:
- Always check existing configurations before making changes.
- Enable TLS 1.2 if you’re looking to meet modern security requirements.
- Restart your system to finalize registry changes.