As organizations continue shifting to cloud services, hybrid identity scenarios (on-premises Active Directory joined devices and Azure Active Directory joined devices) are becoming more common. Microsoft offers a built-in tool called dsregcmd.exe to help troubleshoot and manage these scenarios. This post will explore:
- What
dsregcmd.exeis and why it matters - How to use its most common parameters (e.g.,
/status,/join,/leave) - The importance of the
/debugflag for troubleshooting
Whether you’re decommissioning a device, dealing with registration errors, or just want to streamline your hybrid environment, dsregcmd.exe is an essential utility.
Table of Contents
What Is dsregcmd.exe?
dsregcmd.exe is a command-line tool included with Windows 10 (and later) and Windows Server 2016 (and later). It allows administrators to:
- Check the device’s join state (Azure AD joined, on-prem domain joined, or both)
- View and Diagnose Azure AD registration information
- Join or Leave Azure AD
- Troubleshoot issues related to device registration
You can run it in a standard Command Prompt or PowerShell console. Some tasks require Administrator privileges, so it’s recommended to run your console as Administrator whenever you’re modifying system registration settings.
Basic Commands
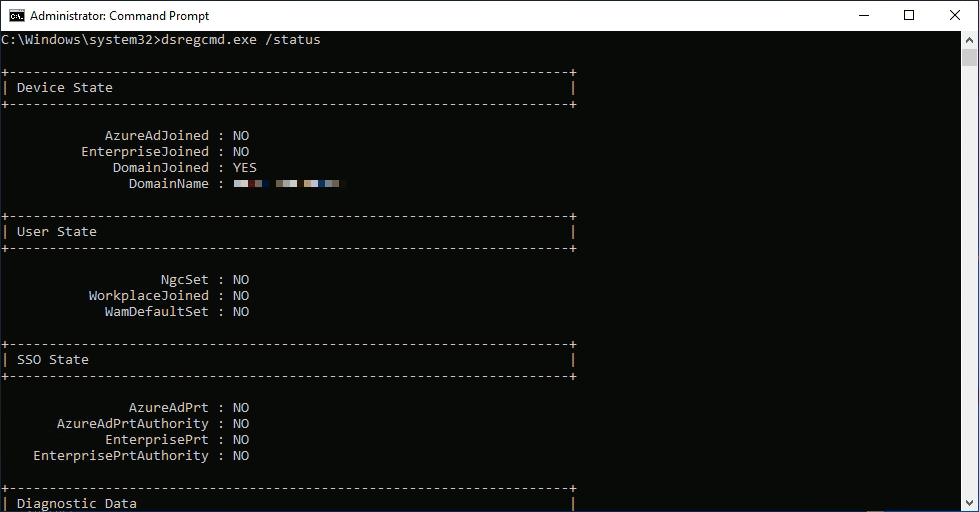
1. dsregcmd /status
This command provides an overview of the device’s current registration state. You’ll see whether the system is joined to Azure AD, the status of Workplace Join, and token information.
dsregcmd.exe /status
- Useful For: Quickly verifying if your device is Azure AD Joined, Hybrid Azure AD Joined, or Workplace Joined.
- When to Use: If users are having trouble accessing cloud resources, or if you suspect a device’s Azure AD join state is out of sync.
2. dsregcmd /join
While typically Group Policy or Intune handles device registration automatically, you can attempt to initiate an Azure AD join manually using /join.
dsregcmd.exe /join
- Useful For: Forcing a device to join Azure AD if the automatic join process failed or if you removed it previously.
- When to Use: In testing scenarios or when an auto-join process didn’t complete successfully.
3. dsregcmd /leave
If you need to unjoin a device from Azure AD, /leave does just that. It removes all Azure AD-related registration details from the device.
dsregcmd.exe /leave
- Useful For: Decommissioning devices, resetting corrupt or partial joins, or preparing a device for re-registration to another tenant.
- When to Use: If you’re repurposing a device, or if the device is stuck in a problematic hybrid join state.
Adding /debug for Troubleshooting
The /debug switch adds verbose output to any command you run with dsregcmd.exe. This is invaluable for troubleshooting because it shows detailed logging messages, error codes, and step-by-step output.
Common Debug Scenarios
- Analyzing Registration Failures: If a device fails to register or join,
/debugcan reveal where the process stops or which error code occurs. - Validating Configuration: After a change in Group Policy or Intune configuration, use
/debugto confirm that all steps complete successfully. - Deep-Dive Troubleshooting: If an application or service requires Azure AD device registration, checking
dsregcmdwith/debugcan help pinpoint misconfigurations.
Examples
- Getting a detailed status report:
dsregcmd.exe /status /debug - Removing a device with full logging:
dsregcmd.exe /leave /debug
dsregcmd.exe /debug /leave
Putting both commands together, /debug and /leave, can be especially helpful in complex environments. Here’s why:
- Verbose Logging: When leaving Azure AD, any configuration or token removal issues will be logged, helping you identify if something goes wrong.
- Clean Removal: You’ll ensure the device is fully disconnected from Azure AD, avoiding partial or “ghost” states that can interfere with re-registration.
- Diagnostic Insight: If the unjoin process fails or leaves artifacts behind, the debug logs will show you exactly which step was problematic.
Steps:
- Open PowerShell as Administrator
- Run:powershellCopyEdit
dsregcmd.exe /debug /leave - Check the Logs: If you run into issues, investigate Event Viewer → Applications and Services Logs → Microsoft → Windows → User Device Registration for detailed logs.
Best Practices & Tips
- Backup or Document Before Changes
Always document the current device state (e.g., rundsregcmd /status) before making changes. This makes it easier to revert or pinpoint problems if something goes wrong. - Reboot
After leaving or joining Azure AD, a reboot might be necessary to ensure all services and tokens are updated. - Automate Where Possible
For large deployments, consider scriptingdsregcmdcommands in PowerShell to handle batch operations on multiple devices. This is particularly helpful when decommissioning or re-registering many systems. - Check Intune or Group Policy
Some organizations have auto-registration policies. If your device repeatedly re-registers after you run/leave, confirm that Group Policy or Intune isn’t automatically re-joining it. - Monitor Your Azure AD Portal
In the Azure AD Admin Center (under Devices), verify whether the device is still registered or showing as “Unknown.” Sometimes replication or sync delays can cause temporary confusion about the device’s state.
dsregcmd.exe is a powerful yet often overlooked tool for managing Azure AD device registration. Whether you’re simply trying to confirm a device’s join state with /status, or force a device to leave Azure AD using /leave, it’s essential to know how each command works. And if you need deeper insight—especially while resolving errors—don’t forget the /debug switch.
Key Takeaways:
- Use
/statusto quickly check registration states. - Use
/joinor/leaveto manage Azure AD device memberships. - Use
/debugto gain full visibility into the process.
By combining these commands effectively, you’ll be well-equipped to keep your Windows devices aligned with your Azure AD environment, troubleshoot issues, and maintain a secure, well-managed infrastructure.